- SecureMyOrg - Security From Around The Globe
- Posts
- Newsletter #11 - May 21, 2024
Newsletter #11 - May 21, 2024

CyberSecurity 101
Hey everyone, high fives for making it to Week 11 of our Cyber Security 101 Series! We've tackled some technical heavy-hitters, and now it's time for something a little more... choose-your-own-adventure! 🏃💨
Here's the question: Have you ever wondered what kind of cybersecurity superhero you could be?
There are tons of exciting specializations within the cybersecurity field, each offering unique challenges and opportunities. Do you dream of becoming a digital detective, hunting down cybercriminals? Or maybe you're a code warrior, passionate about building impenetrable defenses?
The best part? We'll be exploring these different paths in this newsletter! Read on to discover your inner cybersecurity persona and the certifications that can take you there.
🧑🏭 Jobs & Internships
Flipkart seeks an Application Security Engineer (3-5 years experience) to conduct security assessments, identify vulnerabilities, and develop solutions (experience with web/mobile app security testing, penetration testing, and coding a plus).
GoDaddy seeks a Senior Application Security Engineer (8+ years experience) to identify and remediate security threats in applications, with expertise in code review, cloud security (AWS), and secure development lifecycle.
Udemy seeks an Application Security Engineer (2+ years experience) to design and implement secure features, write secure code, and collaborate with cross-functional teams.
SMRT Corp seeks a Cyber SOC Analyst Intern (no experience required) to monitor security alerts, collaborate on incident response, and learn about cybersecurity technologies (SIEM, EDR, ETP).
PwC Singapore seeks a Data Analytics Intern (Computer Science/Engineering/IT student) to assist with IT security reviews, data analytics projects, and learn about cybersecurity trends (no experience specified).
🔏 Last Week in Cyber Security
Join our Discord to get more news in the Security Domain. 🛡️
Bug Bounty Programs vs VDPs: Be Nice, Play Fair
This article defends Vulnerability Disclosure Programs (VDPs) as valuable for both security researchers and software vendors. VDPs allow researchers to test their skills legally and gain recognition, while helping vendors improve security. The author criticizes some researchers who disrespect VDPs and expect payment when it's not offered. The article concludes with a call for cooperation between both sides.
Git Releases Security Fix to Protect Against Remote Code Execution Vulnerability
Git project released version 2.45.1 to fix five security vulnerabilities affecting Windows, macOS, Linux, and BSD systems. Upgrading to the latest version is critical, especially for users who clone repositories from untrusted sources. The update also includes defense-in-depth improvements to prevent future vulnerabilities.
FBI Shuts Down Notorious Hacking Forum BreachForums
The FBI seized BreachForums, a website used by cybercriminals to sell and leak stolen corporate data. Law enforcement believes they have access to user data and are encouraging victims to come forward with information. BreachForums is the successor to several other seized forums including RaidForums. This takedown comes after a recent leak of data stolen from a Europol portal.
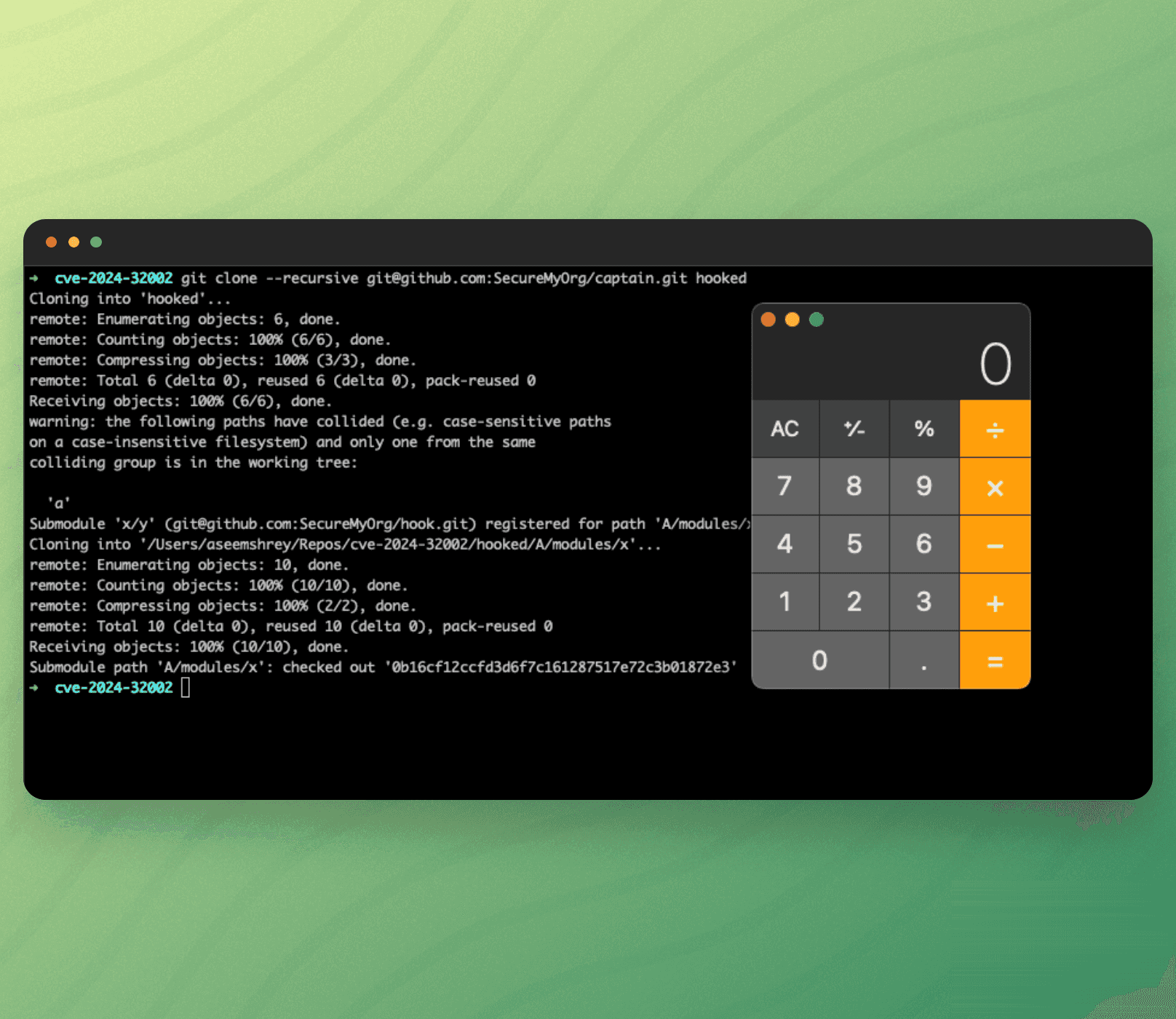
Git RCE - CVE 2024-32002
Hey there!
Heads up about a nasty bug in Git that just got squashed (CVE-2024-32002). This one let attackers sneak malicious code into your computer just by you cloning a booby-trapped repository. Yikes! 🫢
Here's the gist: Git submodules had a glitch that allowed attackers to hide a sneaky script (a post-checkout hook) in your Git directory when you cloned something. This secret script could then run code on your machine without you even knowing it.
The good news is there's a fix.
Check out our blog for a deep dive into this bug!
Different Cybersecurity Specializations and Career Paths
Cybersecurity encompasses a wide range of specializations, each focusing on specific aspects of protecting digital assets and infrastructure.
Some common cybersecurity career paths include:
Security Analyst: Monitoring and analyzing security incidents, conducting risk assessments, and implementing security controls.
Ethical Hacker/Penetration Tester: Identifying vulnerabilities in systems and applications through ethical hacking and penetration testing.
Security Engineer: Designing, implementing, and managing security solutions, such as firewalls, intrusion detection systems, and encryption protocols.
Incident Responder: Investigating and mitigating security incidents, coordinating incident response efforts, and implementing remediation measures.
Security Architect: Designing and planning the overall security architecture of an organization, including network security, cloud security, and identity management.
Check out this diagram for an interactive illustration of different career paths you can take in Cyber Security:
📜 Educational Paths: Degrees, Certifications, Bootcamps There are various educational paths you can take to pursue a career in cybersecurity:
Bachelor's Degree: Many cybersecurity roles require a bachelor's degree in cybersecurity, computer science, information technology, or a related field.
Master's Degree: A master's degree in cybersecurity or a specialized field within cybersecurity can provide advanced knowledge and skills.
Certifications: Industry-recognized certifications, such as CompTIA Security+, Certified Ethical Hacker (CEH), Certified Information Systems Security Professional (CISSP), and Offensive Security Certified Professional (OSCP), can enhance your credentials and marketability.
Bootcamps: Short-term, intensive training programs like cybersecurity bootcamps offer hands-on experience and practical skills development in a condensed timeframe.
✍️ Building a Strong Cybersecurity Portfolio with Practical Experience In addition to formal education and certifications, gaining practical experience is essential for building a strong cybersecurity portfolio.
Consider the following strategies:
Internships and Entry-Level Positions: Seek internships or entry-level positions in cybersecurity to gain real-world experience and exposure to different aspects of the field.
Volunteer Work and Open Source Projects: Contribute to open source cybersecurity projects or volunteer for nonprofit organizations to expand your skill set and network with professionals in the industry.
Personal Projects and Labs: Set up a home lab environment to practice cybersecurity techniques, conduct experiments, and develop your skills in a hands-on setting.
Continuing Education: Stay updated on the latest cybersecurity trends, technologies, and best practices through online courses, workshops, and professional development opportunities.

💡 Did You Know? 💡
The original "white hat" hacker
In the 1970s, a young programmer named John Draper, better known as "Cap'n Crunch," accidentally discovered a whistle in a cereal box that emitted a tone at the same frequency as the system used by phone companies to switch long-distance calls. This discovery allowed him to make free calls. Draper's actions, while technically illegal, exposed a major security flaw in the phone system. He later went on to work for security firms, highlighting the valuable role "white hat" hackers play in identifying and fixing vulnerabilities.
I hope this quick rundown of CyberSecurity Career Paths in our newsletter helped you get an idea of where in the Security Sector you want to be. Just remember that whatever path you choose to take, it is important to do research and know more about the role.
By exploring different cybersecurity specializations, pursuing relevant education and certifications, and gaining practical experience through internships, projects, and volunteering, you can embark on a rewarding career path in cybersecurity. 😀🥳

Reply